I installed tutum/ubuntu in local vm's docker. When I login to ubuntu and run below command. Logger 'Test Logging' I can't find the file where this logged in. In my local system I can see the system.log or syslog or messages file in /var/log. But when I check /var/log in container, I can't find any file like this. Why use syslog-ng for collecting Docker logs? Docker already provides many drivers for logging, even for central log collection. On the other hand, remote logging drivers arrive with a minimalist feature set and you are not able to use the “doc.
Using Seq.Input.Syslog, Seq is able to ingest syslog messages — both RFC3164 and RFC5424 formats — as structured logs.
Contents

What is syslog?
Syslog message formats
RFC 3164
RFC 5424
How to ingest syslog messages into Seq
Method 1: (Windows, Docker) installing Seq.Input.Syslog directly in Seq
Method 2: (Docker) running a separate seq-input-syslog 'sidecar' container
Example usage: analysing NGINX logs with Seq
What is syslog?
Syslog (System Logging) is a logging format and protocol created by Eric Allman as part of Sendmail in the 1980s, and has since gained popularity in *nix based systems — including BSD (Berkeley Software Distrubution) Unix, Linux, and macOS — as well as network devices, such as printers and routers.
Syslog was first standardized by the IETF (Internet Engineering Task Force) in 2001, when the team published a Request for Comments titled 'The BSD Syslog Protocol' (RFC 3164). 'The Syslog Protocol' (RFC 5424), a more modern syslog standard, was later published in 2009, and obsoleted RFC 3164.
Seq.Input.Syslog is able to parse message formats described in both RFC 3164 and RFC 5424, with a few important things to note.
Firstly, Seq.Input.Syslog currently only supports receiving syslog messages over UDP. Secondly, the MSG component of syslog messages sent to Seq via Seq.Input.Syslog are not currently parsed — even if they contain structured elements, they are sent to Seq as free text.
Finally, we do not recommend using Seq.Input.Syslog as a first choice for most use-cases, as there are more convenient log formats that also add structure to the MSG portion of the log. We hope syslog support does help those who maintain and support systems that rely on syslog.
Syslog message formats
Even though RFC 3164 has been obsoleted by RFC 5424, the older log format is still supported in many applications. Seq.Input.Syslog supports structured events for both versions.
Here is a handy reference for both log formats.
RFC 3164
Take the following RFC 3164-formatted syslog message
This message is made up of several important 'parts'.
Below is our simplified explanation of Section 4.1 syslog Message Parts in RFC 3164.
PRI— or 'priority', is a number calculated from Facility (what kind of message) code and Severity (how urgent is the message) code:PRI = Facility * 8 + SeverityTIMESTAMP— format isMmm dd hh:mm:ssHOSTNAME— must contain the hostname, IPv4 or IPv6 address of the message senderMSGis made up of two parts:TAG— the name of the program or process that generated the message. Usually followed by a:or a[pid]:(the beginning of the MSG CONTENT)CONTENT— the details of the message
These parts are parsed into structured log messages in Seq using the Seq syslog input. Here's what the above message looks like in Seq:
RFC 5424
Here is an example RFC 5424-formatted syslog message
Again, this message is made up of important 'parts'. These parts are explained in the next section.
RFC 5424 messages contain more parts than RFC 3164, probably due to no longer being limited to maximum 1024 byte message size.
This is our simplified explanation of Section 6. Syslog Message Format in RFC 5424.
HEADERPRI— or 'priority', is a number calculated from Facility (what kind of message) code and Severity (how urgent is the message) code:PRI = Facility * 8 + SeverityVERSION— version is always '1' for RFC 5424TIMESTAMP— valid timestamp examples (must follow ISO 8601 format with uppercase 'T' and 'Z')1985-04-12T23:20:50.52Z2003-08-24T05:14:15.000003-07:00-('nil' value) if time not available
HOSTNAME— using FQDN (fully qualified domain name) is recommended, e.g.mymachine.example.comAPP-NAME— usually the name of the device or application that provided the messagePROCID— often used to provide the process name or process ID (is-'nil' in the example)MSGID— should identify the type of message, more detail in RFC 5424 Section 6.2.7. MSGID
STRUCTURED-DATA— named lists of key-value pairs for easy parsing and searching, more detail in RFC 5424 Section 6.3. STRUCTURED-DATAMSG— details about the event- if the
MSGis encoded in UTF-8, the string must start with the Unicode byte order mask (BOM), more detail in RFC 5424 Section 6.4. MSG
- if the
And here's what the same RFC 5424 formatted message looks like in Seq:
How to ingest syslog messages into Seq
There are two ways to send syslog messages to Seq:
- by installing
Seq.Input.Syslogdirectly in Seq (Windows and Docker), or - by running a separate
seq-input-syslog(Docker only).
Below is a convenient shell command to test if your setup is working, while you're getting set up with Seq.Input.Syslog, you can use this test syslog message to check everything is configured correctly (if your system has netcat):
Method 1: (Windows, Docker) installing Seq.Input.Syslog directly in Seq
The simplest method is
- installing
Seq.Input.Syslogdirectly in Seq via Settings > Apps, and then - set up an instance (i.e. syslog receiver) using the
Add Instancebutton in Apps
If you are running Seq as a Windows service, you must first check that your chosen syslog listener port is allowed through Windows firewall (UDP port 514 is the default, but you can pick a different UDP port).
If you are running Seq in Docker, you must first expose your chosen syslog listener port via your docker run command or docker-compose file. Remember, this is only required if you are installing Seq.Input.Syslog in Settings > Apps. Here's a docker run datalust/seq command with the correct ports exposed:
If you are running Seq in Docker, we recommend you choose the seq-input-syslog sidecar container method, where you do not need to expose any extra ports on the seq container, and will also save you the extra app installation steps.
Method 2: (Docker) running a separate seq-input-syslog 'sidecar' container
For Seq to ingest syslog messages, you can deploy datalust/seq-input-syslog as a Docker container alongside a separate Seq instance.
The seq-input-syslog container receives syslog messages (via UDP on port 514 by default), and forwards them to the Seq ingestion endpoint specified in the SEQ_ADDRESS environment variable.
Here's a docker run datalust/seq-input-syslog command with the default UDP listener port exposed, and sends logs to a Seq ingestion endpoint at https://seq.example.com:5341:
Example: analysing NGINX logs with Seq
Installing Syslog On The Raspberry Pi Using Syslog-NG
Here is an example docker-compose.yml which uses Docker's syslog log driver to forward NGINX docker container logs to Seq (i.e. whatever you see in stdout when you run docker logs -f <container-name>).
Important note: This is not our recommended way to get NGINX logs into Seq. Instead, use Seq.Input.GELF.
Why is localhost allowed for the logging-driver syslog-address? This is because the logging driver daemon is actually on the host machine, and localhost is resolved outside of the docker container.
Here is what an NGINX log looks like in Seq, after accessing localhost:8888:
Docker Syslog Server Gui
That's it! Hope you're up and running in minutes with Seq as your new centralized syslog server :)
If you have any feedback or would like to contribute, please create a GitHub issue for Seq.Input.Syslog.
Happy logging! ❤️
It wasn’t long ago when organizations cited several concerns and excuses to avoid putting their production workloads in containers. Things have changed, to say the least. With Docker, container technology has gained high acceptance, and users now download millions of container images daily.
Docker containers offer an efficient and convenient way to ship software reliably, without posing the traditional challenges developers encountered during the movement of software from production to the live environment. As all configuration files, libraries, and dependencies required to run the application are clubbed together with the application in a container, it becomes easy to ship the software without any worries.
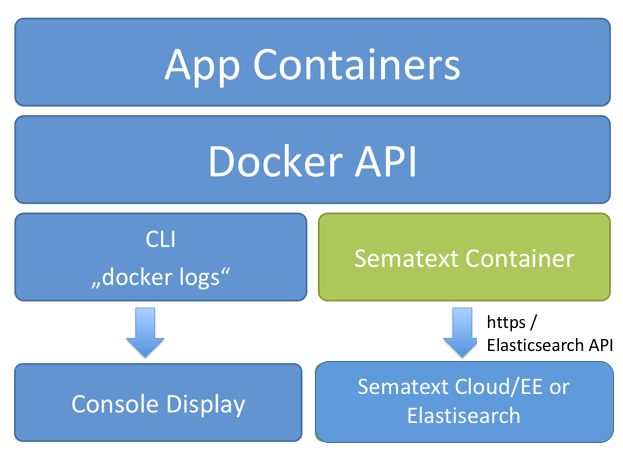
Despite all its positives, Docker isn’t the silver bullet for everything that can go wrong with an application. When an issue arises, developers or DevOps professionals need access to logs for troubleshooting. This is where things get a little tricky. Logging in Docker isn’t the same as logging elsewhere. In this article, we’ll discuss what makes logging in Docker different, along with the best practices for Docker logging:
Challenges With Docker Logging
Unlike traditional application logging, there are several methods for managing application logs in Docker. Organizations can use data volumes to store logs as the directory can hold data even when a container fails or shuts down. Alternatively, there are several logging drivers available, which after minor configuration, can allow teams to forward their log events to a syslog running on their host. For first time users, identifying which of these methods would suit their requirement isn’t always straightforward.
One had to consider the limitations of every method. For instance, when using logging drivers, one can face challenges in log parsing. Inspecting the log files with “docker logs” command isn’t possible in every case, as it works only with json-file logging driver. Further, Docker logging drivers don’t support multi-line logs.
Moreover, complexity increases while managing and analyzing a large number of container logs from Docker Swarm. Very often, containers start multiple processes, and the containerized applications start generating a mix of log streams containing plain text messages, unstructured logs, and structured logs in different formats. In such cases, parsing of logs becomes challenging, as it isn’t simple to map every log event with the container or app producing it.
Docker Syslog Location
Creating centralized log management and analytics setup or using a cloud-based solution like SolarWinds® Papertrail™ can help in solving the above challenges. Papertrail simplifies log management with a quick setup and support for all common logging frameworks for log ingestion. It parses your logs and streamlines troubleshooting with simple search and filtering. You can tail logs and view real-time events in its event viewer, which provides a clean view of events in infinite scroll with options to pause the feed or skip to specific time frames. Check out the plans or get a free trial of Papertrail here.
Given below some tips and best practices for logging in Docker.
Best Practices for Docker Logging
- Centralized Log Management
Docker Syslog Rsyslog
There was a time when an IT administrator could SSH into different servers and analyze their logs using simple grep and awk commands. While the commands still function as before, due to the complexity of modern microservices and container-based architectures, traditional methods for log analysis aren’t sustainable anymore. With several containers producing a large volume of logs, log aggregation and analysis become highly challenging.
What Is The System Log (Syslog)? - Definition From Techopedia
This is where cloud-based centralized log management tools help in efficient and effective analysis of such logs. Moreover, one can also use the same tools to manage infrastructure logs (containerized infrastructure services, Docker Engine, etc.). With both application and infrastructure logs in one place, teams can easily monitor their entire ecosystem, correlate data, find anomalies and troubleshoot issues faster.
- Customization of Log Tags
It’s not an easy task to monitor an endless stream of logs and find relevant information for the resolution of issues. To make things simple while collecting logs from a large number of containers, organizations can tag their logs using the first 12 characters of the container ID. The tags could be customized with different container attributes to simplify the search.
- Security and Reliability
With modern log analysis tools, it’s easier to run full-text searches over a large volume of log data and get quick results. However, application logs can contain a lot of sensitive data, which shouldn’t fall into the wrong hands. Messages sent via syslog connection should be encrypted to avoid this from happening.
While using a syslog driver with TCP or TLS is a reliable method for the delivery of logs, temporary network issues or high network latency can interrupt real-time monitoring. It’s seen often when the syslog server is unreachable, Docker Syslog driver blocks the deployment of containers and also loses logs. To avoid this, teams can install the syslog server on the host. Alternatively, they can also use a dedicated syslog container, which can send the logs to a remote server.
- Real-Time Response
For real-time monitoring, teams can use docker logs command’s –follow option. The feature is similar to the conventional -tail command, and helps in viewing log files in production environments to identify issues proactively. Log management tools like SolarWinds Loggly® and Papertrail can further simplify real-time monitoring from multiple sources, with unified dashboards giving a quick overview of the environment. Further integrating the log management solution with notification tools like Slack, PagerDuty, Victorops, etc, is also crucial. With notifications, IT administrators can configure intelligent alerts to stay on top of their Docker application logs.
Top Tools for Docker Log Management
Open Source Tools: Organizations can develop robust log monitoring and analytics set up using various open-source tools. These tools may pose some configuration challenges, but strong community support can help address such issues. For instance, they can consider Telegraf / syslog + docker syslog driver for log collection, Influx DB for storage, and Grafana and Chronograf to create a user interface. Also, there are several guides available to use ELK stack (Elastic Search, Logstash, and Kibana) for Docker monitoring.
Commercial Tools: While an open-source tool for log management and analysis may appear to be a lucrative option, it can take up a lot of time and effort to set up a Docker log viewer. This is where commercial tools often have an advantage, as they come with dedicated support. Tools like Dynatrace, Papertrail, Loggly, Logentries, Sentry also offer several advanced features to simplify troubleshooting. Further, most of these tools offer a free evaluation period.